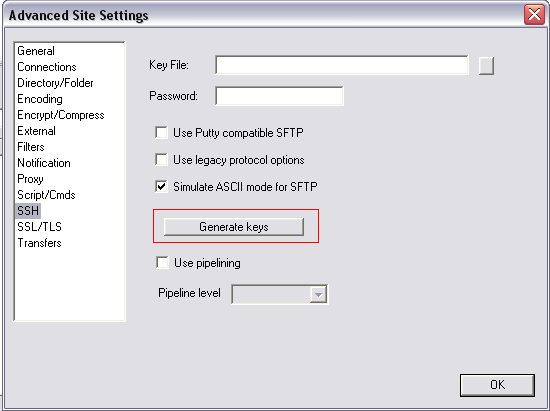
Step 1: Advanced site settings -> ssh
SSH key pairs allow an additional level of security that can be used in conjunction with the SFTP protocol.
Key pairs are typically created by the client, and then the resulting public key is used by Core FTP Server.
Core FTP products use the OpenSSH SSH2 format, that can be generated using Core FTP software, or via the ssh-keygen utility.
Core FTP client -- creating a key pair
Step 1: Advanced site settings -> ssh

Step 2: Entering key information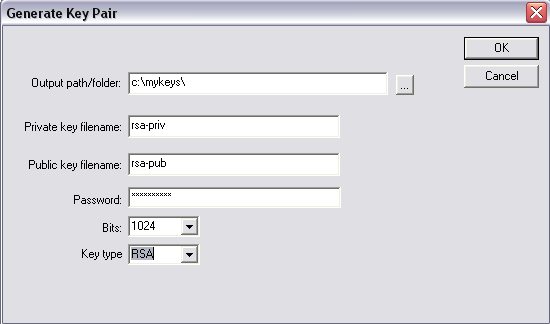
Step 3: Selecting private key into client site profile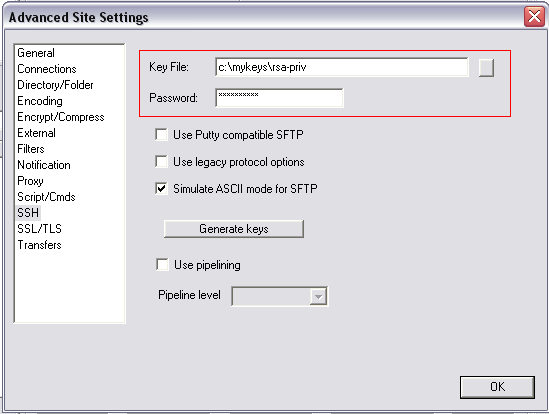
Additionally if no account password is being used for the server, check the Advanced -> General -> "Don't prompt for password when empty" option.
ssh-keygen usage: (Unix/Linux)
rsa keys: ssh-keygen -t -m PEM
dsa keys: ssh-keygen -t dsa -m PEM
If your private key file starts with:
-----BEGIN OPENSSH PRIVATE KEY-----
the private key will need to be converted to OpenSSL PEM format:
ssh-keygen -p -f /path/to/your/key -m pem
For Unix/Linux, dsa keys may be the preferred method due to better compatibility across operating systems.
Putty users using psftp need to export OpenSSH public keys using Puttygen
Entering public key into Core FTP Server
Once you have created a key pair, the public key file is then placed in a directory on the server that cannot be accessed by the client account.
Select the public key file in the Core FTP Server's user "security properties", in the "ssh pub cert" field.
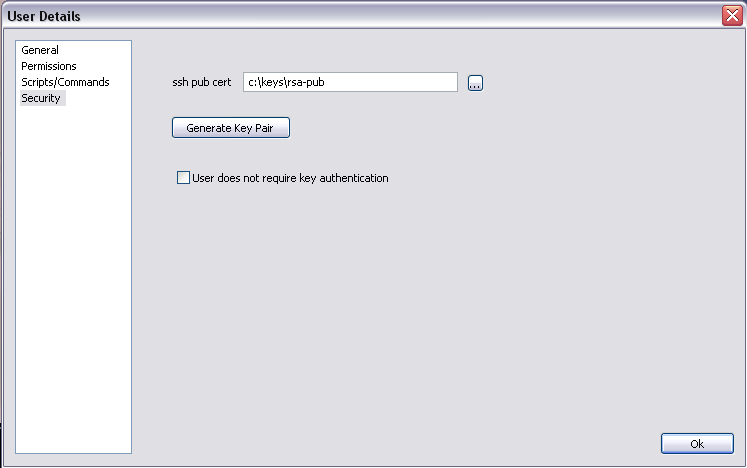
The server will need the "Allow key authentication" option checked in the domain setup.
For SSH key pairs and no account password, the "Key authentication only" option should be checked. Users not using keypairs can bypass the public key requirement by selecting the "User does not require key authentication" in the user's "security" settings.
Example of a public key (file contents):
AAAAB3NzaC1yc2EAAAABIwAAAIEA153PICRN2+viqQ2570jEfUPcWgknD079wX/QtdF0lIbMaOYeMba9jf/qqmfuWYSybNmpSxMZiyjbKDvH+iZ/iT0MwrK9x19Zkjb8nXugWtOOJSwiHc48DSwMkLDdbVdG/BvstHbBquBdQNkJz+VDxFO+P3TcfYbIsvx+YFxnbLU=
or
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEA153PICRN2+viqQ2570jEfUPcWgknD079wX/QtdF0lIbMaOYeMba9jf/qqmfuWYSybNmpSxMZiyjbKDvH+iZ/iT0MwrK9x19Zkjb8nXugWtOOJSwiHc48DSwMkLDdbVdG/BvstHbBquBdQNkJz+VDxFO+P3TcfYbIsvx+YFxnbLU=
The '=' character should be the last character in the public key. Multiple keys can be in one file, one per line.
Begining characters identifying the key type at the beginning (rsa or dsa) are acceptable and read by Core FTP Server.
Keys should be in multibyte format.
Core FTP software utilizes SSH2 and greater versions of SSH...SSH1 is not supported
Core FTP Server Build 405 and greater supports RFC 4716 SSH formatted keys
ssh keys